[ad_1]
In moral hacking and penetration trying out, password cracking is the most important in gaining get right of entry to to a device or a server.
In methods and databases, passwords are hardly ever stored in plain-text shape.
Passwords are all the time hashed ahead of being saved within the database, and the hash is when put next right through the verification procedure.
Depending at the encryption hired, other methods retailer password hashes in several tactics. And when you’ve got hashes, you’ll simply crack any password.
And on this article, we’ll discover how to crack password hashes the usage of a at hand and very good Hashcat command-line device.
So let’s get began.
But ahead of that…
What is a Hash serve as?
Hashing is the method of changing a typical enter textual content right into a fixed-size string of textual content the usage of some mathematical serve as which is referred to as the Hash Function. Any textual content, irrespective of duration, may also be was a random aggregate of integers and alphabets the usage of an set of rules.
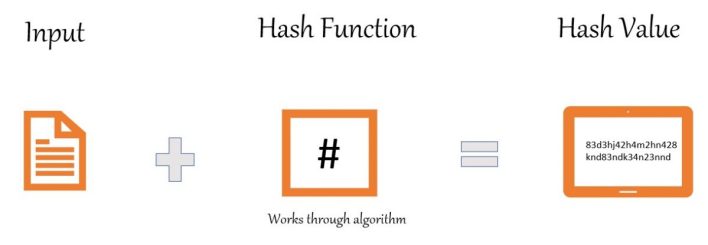
- Input refers to the message that might be hashed.
- The hash serve as is the encryption set of rules like MD5 and SHA-256 that converts a string right into a hash worth.
- And in the end, the hash worth is the outcome.
What is Hashcat?
Hashcat is the fastest password restoration device. It was once designed to ruin the excessive complicated passwords in a brief period of time. And this device could also be succesful of each wordlist and brute power assaults.
Hashcat has two variants. CPU and GPU (Graphical Processing Unit) founded. The GPU-based device can crack the hashes in much less time than the CPU. You can test the GPU motive force necessities on their professional web site.
Features
- Free and open-source
- More than 200 hash sort permutations may also be applied.
- Supports multi-operating methods like Linux, Windows, and macOS.
- Multi-Platforms like CPU and GPU strengthen are to be had.
- Multiple hashes may also be cracked on the similar time.
- Hex-salt and hex-charset recordsdata are supported, together with the automated efficiency tuning.
- A integrated benchmarking device is to be had.
- Distributed cracking networks may also be supported the usage of overlays.
And you’ll see different options additionally from their web site.
Installation of Hashcat
First, be certain your Linux device is up to date with the most recent methods and equipment.
For this, open a terminal and kind:
$ sudo apt replace && sudo apt improveHashcat is generally pre-installed in Kali Linux. You can to find the device below the password cracking phase. But if you wish to have to set up it manually in any Linux distribution, sort the next command within the terminal.
$ sudo apt-get set up hashcatTool Usage
To get began with Hashcat, we’ll want some password hashes. If you don’t have a hash to crack, we can create some hashes first.
To create hashes the usage of the command line, simply observe the under layout.
echo -n "enter" | set of rules | tr -d "-">>outputfienameFor instance, you’ll see I became some phrases into hashes the usage of the md5 set of rules under.
┌──(root💀kali)-[/home/writer/Desktop]
└─# echo -n "geekflare" | md5sum | tr -d "-">>crackhash.txt
echo -n "password123" | md5sum | tr -d "-">>crackhash.txt
echo -n "Webtechnology" | md5sum | tr -d "-">>crackhash.txt
echo -n "microsoftteams" | md5sum | tr -d "-">>crackhash.txt
echo -n "recyclebin" | md5sum | tr -d "-">>crackhash.txtAnd the output might be stored within the crackhash.txt record.
Now we can test the hashes which have been stored within the given record.
┌──(root💀kali)-[/home/writer/Desktop]
└─# cat crackhash.txt
066d45208667198296e0688629e28b14
482c811da5d5b4bcd497ffeaa98491e3
72a2bc267579aae943326d17e14a8048
2192d208d304b75bcd00b29bc8de5024
caae8dd682acb088ed63e2d492fe1e13You can see, now we have now some hashes to crack. This is the process to create a hash via the usage of the set of rules of your selection.
The subsequent step is to kick get started a Hashcat device for your Linux system. Just use the next command to use Hashcat.
$ hashcat --helpIt’ll convey up the entire choices you’ll want to know to run the device. On the terminal, you’ll to find the entire assault and hash modes.
The normal type of the command is
$ hashcat -a num -m num hashfile wordlistfileHere the ‘num’ represents a selected assault and hash mode to use. If you scroll the terminal, you’ll to find the precise numbers for each and every assault and hash mode, like for md4 – the quantity is 0, and for sha256 set of rules – the quantity is 1740.
The wordlist I’m going to use is rockyou wordlist. You can simply to find that wordlist within the trail /usr/proportion/wordlists.
You will even use the find command to to find that wordlist trail.
┌──(root💀kali)-[/home/writer]
└─# find rockyou.txt
And in the end, to crack the hashes the usage of the wordlist record, use the next command.
$ hashcat -a 0 -m 0 ./crackhash.txt rockyou.txtAfter operating this command, you will get a runtime error ( Token duration exception error ) which may also be resolved simply.

To get to the bottom of this, save each and every hash one by one in a special record. This error happens when you’ve got a low CPU or GPU pace. If your laptop has a high-speed processor, you’ll simply crack the entire hashes concurrently a unmarried record itself.
So after solving the mistake and the whole lot, the outcome might be like this.
┌──(root💀kali)-[/home/writer/Desktop]
└─# hashcat -a 0 -m 0 hashcrack.txt rockyou.txt
hashcat (v6.1.1) beginning...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-8265U CPU @ 1.60GHz, 2403/2467 MB (1024 MB allocatable), 4MCU
Minimum password duration supported via kernel: 0
Maximum password duration supported via kernel: 256
Hashes: 1 digests; 1 distinctive digests, 1 distinctive salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff masks, 262144 bytes, 5/13 rotates
Rules: 1
Dictionary cache constructed:
* Filename..: rockyou.txt
* Passwords.: 14344405
* Bytes.....: 139921671
* Keyspace..: 14344398
* Runtime...: 1 sec
8276b0e763d7c9044d255e025fe0c212: [email protected]
Session..........: hashcat
Status...........: Cracked
Hash.Name........: MD5
Hash.Target......: 8276b0e763d7c9044d255e025fe0c212
Time.Started.....: Sun Dec 12 08:06:15 2021 (0 secs)
Time.Estimated...: Sun Dec 12 08:06:15 2021 (0 secs)
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1059.6 kH/s (0.52ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 4096/14344398 (0.03%)
Rejected.........: 0/4096 (0.00%)
Restore.Point....: 0/14344398 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: 123456 -> pampam
Started: Sun Dec 12 08:06:13 2021
Stopped: Sun Dec 12 08:06:16 2021In the above end result, after the dictionary cache main points, you’ll understand, the hash was once cracked, and the password was once published.
Conclusion
I am hoping you have got received a greater working out of the usage of Hashcat to crack passwords.
You will also be concerned with figuring out in regards to the more than a few brute-force equipment for penetration trying out and one of the most highest pentesting equipment.
[ad_2]




